A public key infrastructure (PKI) can be defined as a set of policies, procedures, hardware, software and people that is required to generate, manage, distribute, store, inspect, use, reject and revoke Digital Signature Certificates and manage public-key encryption.
The public key infrastructure facilitates a safe and secure electronic transfer of information for a wide variety of online activities ranging from E-Commerce to internet banking. This is required when a simple password is not enough to verify the identity of a user and a more secure method of proof is needed to make sure that communication and the information that is taking place between the parties is protected.
In cryptography, one will find that PKI uses public keys of the respective user, which is bound utilizing a certificate authority (CA). The Identity of each user is unique within each CA domain. This binding requires registration and issuance process; depending upon the binding, the process can be carried out by software at a CA or under human supervision. RA or registration authority is the PKI role that ensures this binding, and it is responsible for accepting the request of digital certificates and fulfilling the authentication process when a person or organisation demands it.
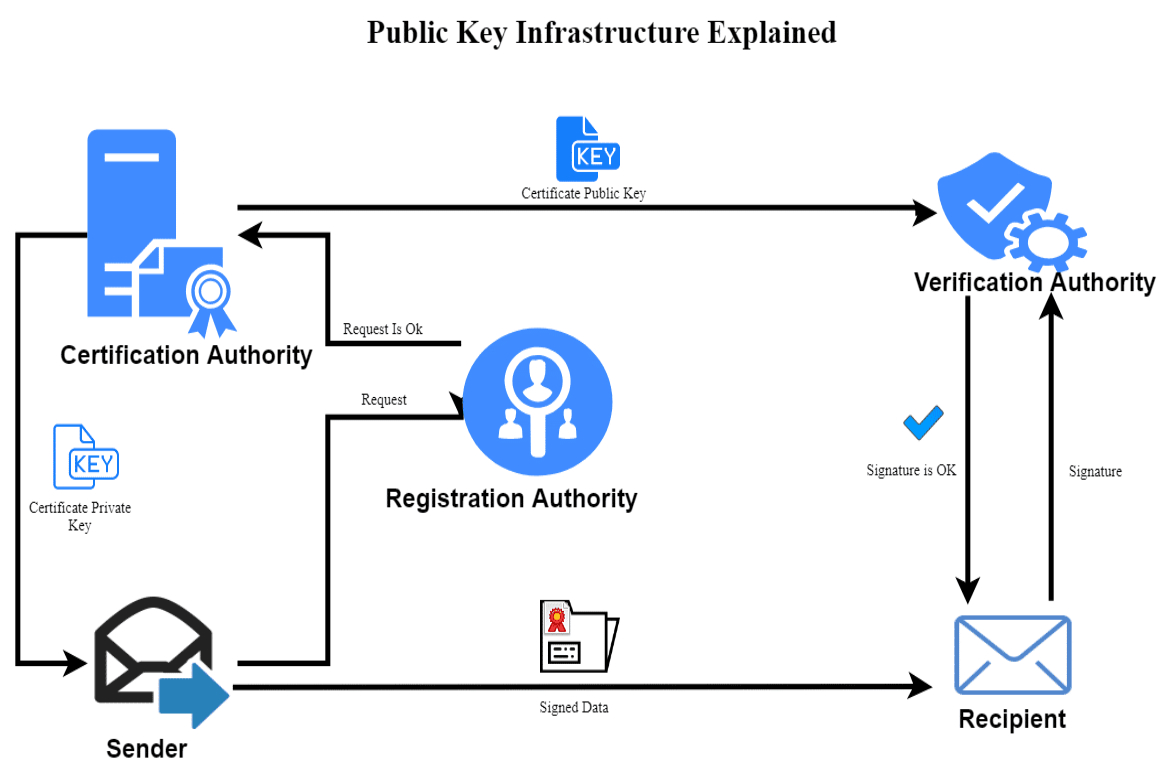
A PKI consists of:
- The issuance and verification of Digital certificate by a certificate authority (CA)
- registration authority that verifies the identity of the users who are requesting information from the certificate authority
- A secure location in which index keys are stored known as a central directory
- A certificate management system along with certificate policy
The certificate contains amongst other information:
- The Identity of the CA
- Identity of the owner
- The public key of the owner
- The expiry date of the certificate
- The signature of the CA on the specific certificate
With years of experience working in cryptography and internetworking, EFILING INFOTECH Technology has been able to shop in their skills to offer solutions built around the PKI, a framework guaranteeing the confidentiality, authentication process, secure network, privacy as well as non-reputation.
The company also provides a wide range of software application based on the cryptographic protocol used as well as algorithms; these products are targeted to address the basic needs of an organisation, in both internal and external processes, by means of the internet.
The cutting edge technology we provide our customers is made with the focus that quick service along with 100% customer satisfaction is the goal.
